DeepSee tracks malicious behaviors across millions of sites each day in order to bring these behaviors to light on our website.We use this data to group sites with similar behaviors, and this article describes a particularly large group of sites which exhibit potentially malicious behavior.
It’s particularly of concern to us when sites forcibly navigate their visitors by means of popups or redirect. Such cases are frustrating & possibly dangerous experience for the user, and also affect advertisers who bid for inventory on the unintended destination page. These types of internet scams are a widespread and chronic occurrence.
Redirects can be useful to fraudsters & bad-faith marketers for a variety of reasons, including:
- Redirected users are real people, and can pass human detection algorithms. Redirected users can be used to fulfill CPM & CPV campaigns
- Link shorteners are one form of redirector; bad actors use link shortners to trick people into visiting domains which may be banned on social media platforms
- Redirects can easily be used to manipulate web traffic rankings. Even users who immediately bounce may influence certain ranking systems
What is the Omni Redirection Network?
The network is made up of over 12,000 unique root domains, many registered in the past few months, which only serve to bounce traffic to 81 unique URLs.
Many of the destination pages are ad-supported, but not all. These 81 destinations seem to have been hand-picked, and they haven’t much changed since January: 11 are Twitter pages belonging to well known right-wing personalities, 12 are videos on Youtube, and ALL are sites which are well-known.
It’s not totally clear to what end this network is being leveraged (we do have some theories, which we will elaborate on in this article), but it IS clear that they navigate visitors forcibly, and often at the expense of advertisers on the page at the time of arrival.
The following image shows a few examples of sites in the Omni Redirect Network:
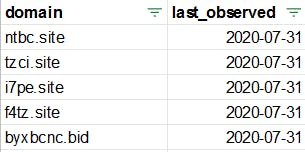
As one can see, they tend to be nonsense combinations of random letters. What they share in common: the destination of the visitor.
The complete list of destination URLs can be accessed here. The following image summarizes the redirect destinations by their root domain & how many unique pages appear as destinations:
The number of domains which matched this profile was under a thousand earlier this year, but that has since exploded to over 12,000.
As the chart shows, the size of the network seems to have stabilized. We have the complete list of active redirectors available for you here.
Publishers will be able to detect when a user arrives on their page by means of the Omni Redirection Network by comparing the HTTP referer header to the list of domains provided.
It is also recommended to add these domains to your ad-block list in order to prevent your browser being hijacked.
As of the time of writing, visiting these domains in most modern browsers does not trigger a warning / prevent forced navigation.
The following video is an example of what it’s like to visit one of these 12,000+ redirectors:
How Does it Work?
Visiting one of the sites in the list of redirectors returns the following HTML:
HTTP/1.1 200 OK
Date: Wed, 12 Aug 2020 19:41:36 GMT
Content-Type: text/html; charset=utf-8
Server: Kestrel
Cache-Control: no-store,no-cache
Pragma: no-cache
Content-Length: 2668
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<title>Home Page</title>
</head>
<body>
<script src="/lib/jquery/dist/jquery.min.js"></script>
<script src="/lib/playcanvas-latest.min.js"></script>
<script type="text/javascript">
function setCookie(name, value, daysToLive) {
// Encode value in order to escape semicolons, commas, and whitespace
var cookie = name + "=" + encodeURIComponent(value);
if (typeof daysToLive === "number") {
/* Sets the max-age attribute so that the cookie expires
after the specified number of days */
cookie += "; max-age=" + (daysToLive * 24 * 60 * 60);
document.cookie = cookie;
} else {
document.cookie = cookie;
}
}
function getCookie(name) {
// Split cookie string and get all individual name=value pairs in an array
var cookieArr = document.cookie.split(";");
// Loop through the array elements
for (var i = 0; i < cookieArr.length; i++) {
var cookiePair = cookieArr[i].split("=");
/* Removing whitespace at the beginning of the cookie name
and compare it with the given string */
if (name == cookiePair[0].trim()) {
// Decode the cookie value and return
return decodeURIComponent(cookiePair[1]);
}
}
// Return null if not found
return null;
}
setCookie('L-M', encodeURIComponent(pc.platform.mobile));
setCookie('L-A', encodeURIComponent(pc.platform.android));
setCookie('L-D', encodeURIComponent(pc.platform.desktop));
setCookie('L-I', encodeURIComponent(pc.platform.ios));
setCookie('L-T', encodeURIComponent(pc.platform.touch));
setCookie('L-W', encodeURIComponent(pc.platform.windows));
setCookie('L-G', encodeURIComponent(pc.platform.gamepads));
setCookie('L-WW', encodeURIComponent(pc.platform.workers));
setCookie('L-X', encodeURIComponent(pc.platform.xbox));
var href = window.location.href;
setCookie('L-R', href);
setCookie('L-AR', 'False');
var referrer = document.referrer;
if (referrer != null) {
setCookie('L-PR', referrer);
}
window.location.href = '/Home/Process';
</script>
</body>
</html>
This script does not do very much, except profile the user & the capabilities of the device from which they are browsing the web.
It uses the PlayCanvas game engine in order to detect if a device meets a few criteria, and sets a cookie value of “True” if it meets these capabilities.
Additionally, it sets a cookie which contains information about where the user is coming from using the HTTP referrer information.
Finally, it sends the user to the ‘/Home/Process’ directory of the site, which handles the destination routing. It is likely that the destination a user will be sent to is based off the criteria stored in the cookies which were just set.
Here is an example of the subsequent request to the ‘/Home/Process’ directory, and the resulting redirect:
GET http://1api.site/Home/Process HTTP/1.1 Host: 1api.site Connection: keep-alive Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://1api.site/ Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: L-M=false; L-A=false; L-D=true; L-I=false; L-T=false; L-W=false; L-G=true; L-WW=true; L-X=false; L-PR=; L-R=http%3A%2F%2F1api.site%2F; L-AR=False
HTTP/1.1 302 Found Date: Wed, 12 Aug 2020 19:41:36 GMT Server: Kestrel Content-Length: 0 Cache-Control: no-store,no-cache Pragma: no-cache Location: https://www.msnbc.com/msnbc/watch/a-panel-talks-the-nyt-report-on-trump-kushner-and-deutsche-bank-59946565595
Pulling Back the Curtain on Omni
The vast majority of redirector domains have obfuscated registration information, this makes tracking down the source of this internet scam tricky. It’s clear that the operator doesn’t want to be subject to scrutiny.
Still, there are several pieces of information which were left public that make it abundantly clear who registered & manages this fleet of redirectors.
In pulling threads, we learned a surprising amount about these entities, which we are sharing here today to give some context.
1. Not All Domain Registry Services are Created Equal
Given the randomness of the domains, and the fact that they span across hundreds of TLDs (.com, .co.uk, .eu, etc…), it’s likely the 12,000+ redirectors were registered programmatically, and not completely subject to human review by the registrants.
Perhaps unaware to the registrants, a handful of domains were registered as “.jp” entities; the “.jp” registry does not allow for privacy protection, and this tipped us off to exactly who the registrants were.
The following images show the 2 unique registrants related to domains in the Omni Redirector network
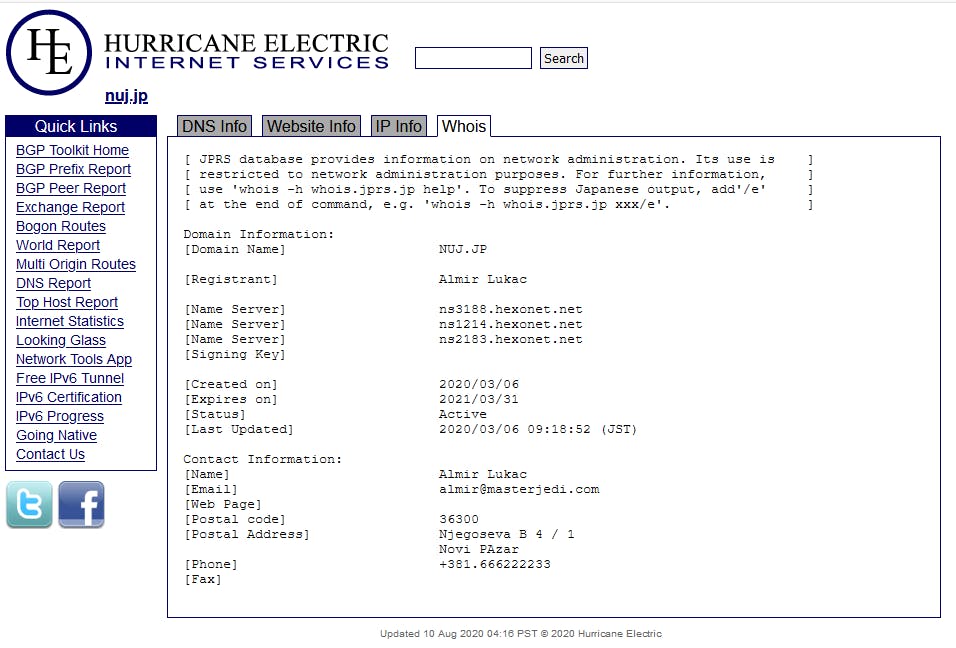
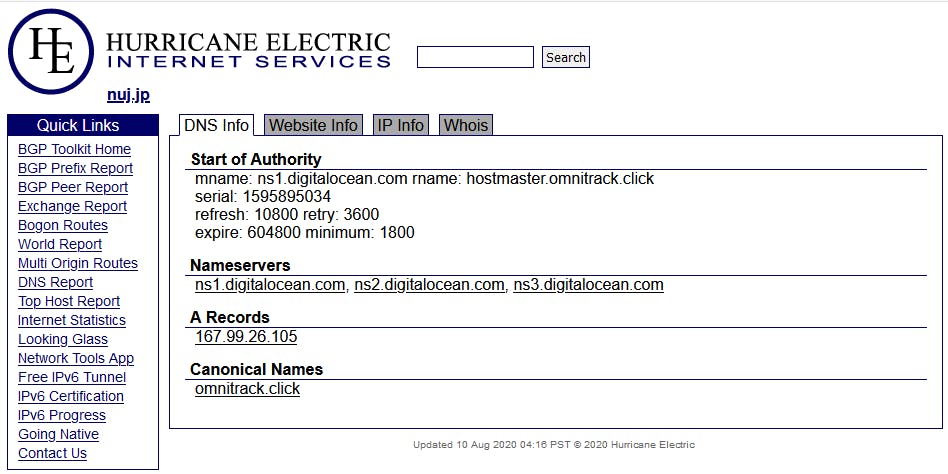
nuj.jp, registered by Almir Lukac
———————————————————-
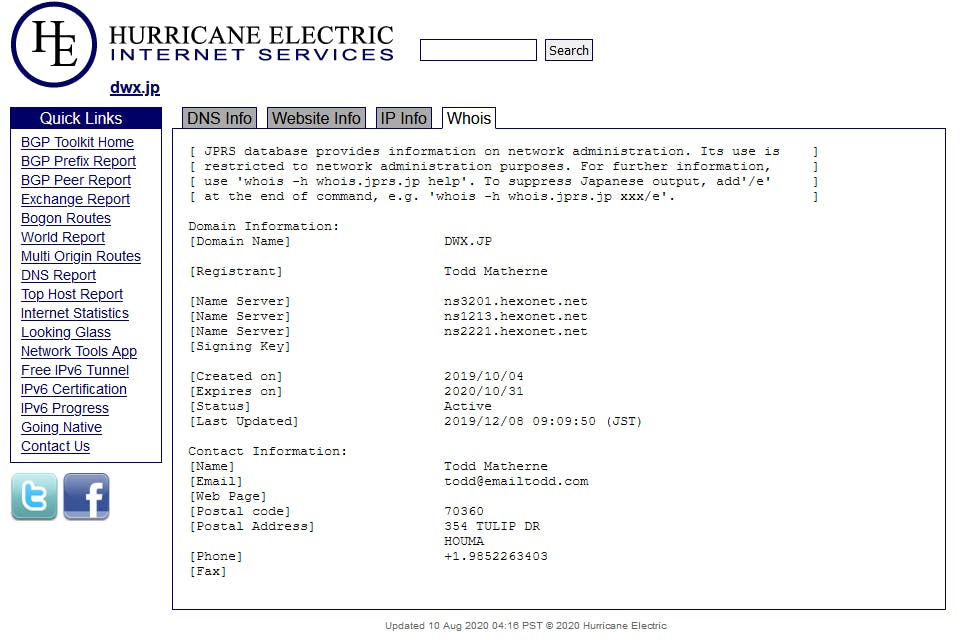
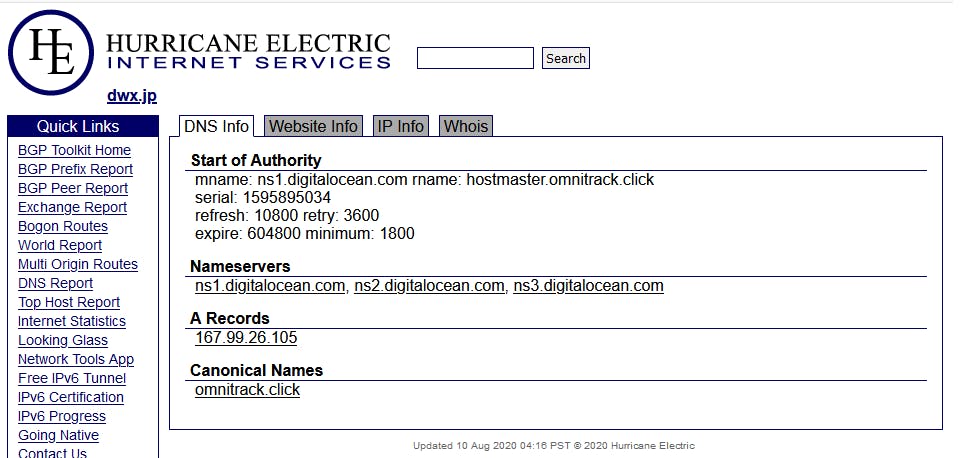
dwx.jp, registered by Todd Matherne
We can see that both domains share an IP address, and a Canonical Name (CNAME) , which specifies an alias or nickname for a host name record in a domain name system (DNS) database. The shared CNAME is “omnitrack.click“, and the associated IP address is 167.99.26.105.
In fact, upon closer review, we found nearly ALL the domains in this scheme could be linked to 167.99.26.105 ; visiting this IP in your browser will trigger the same behavior as any of the 12,000 individual domains.
2. Todd + Almir = ???
We have email addresses associated with each registrant, but they are not from the same organization. What is the link between these two?
A simple google search for our two registrants makes things a bit more clear:
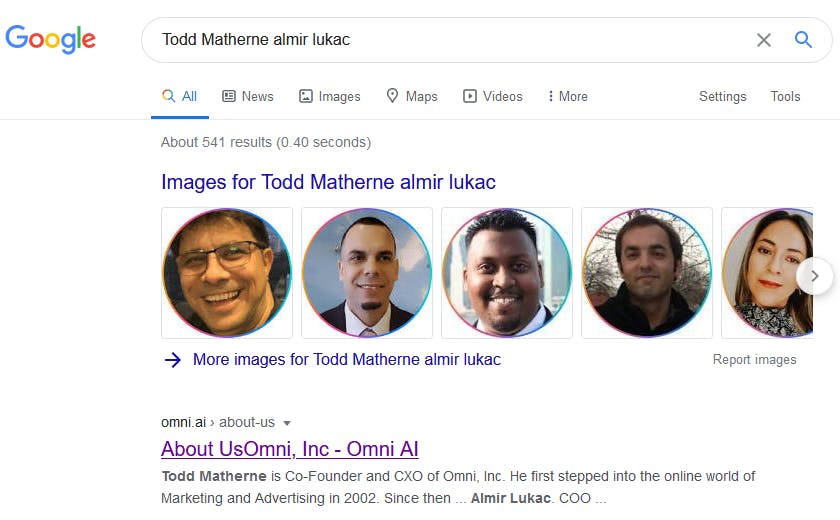
It seems that both registrants are featured in the “about us” section of a site: omni.ai
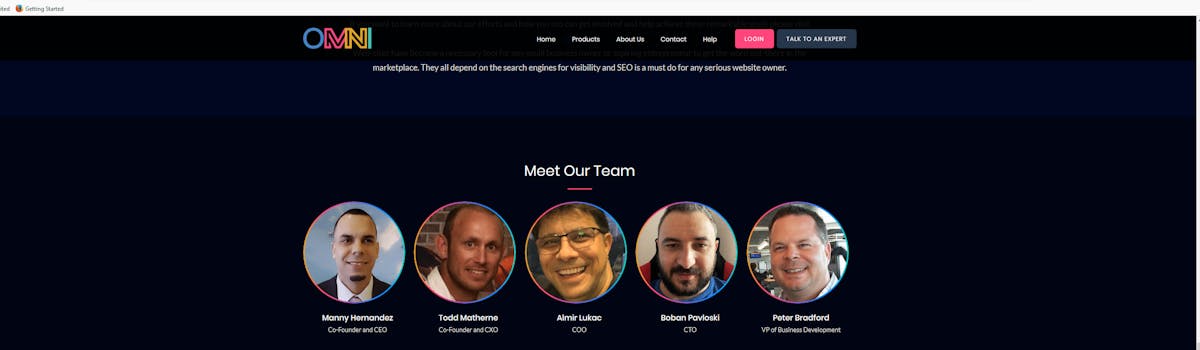
Now you may see where this network of redirectors gets its name; both registrants are part of Omni AI, where Manny Hernandez is the CEO.
3. What is Omni AI?
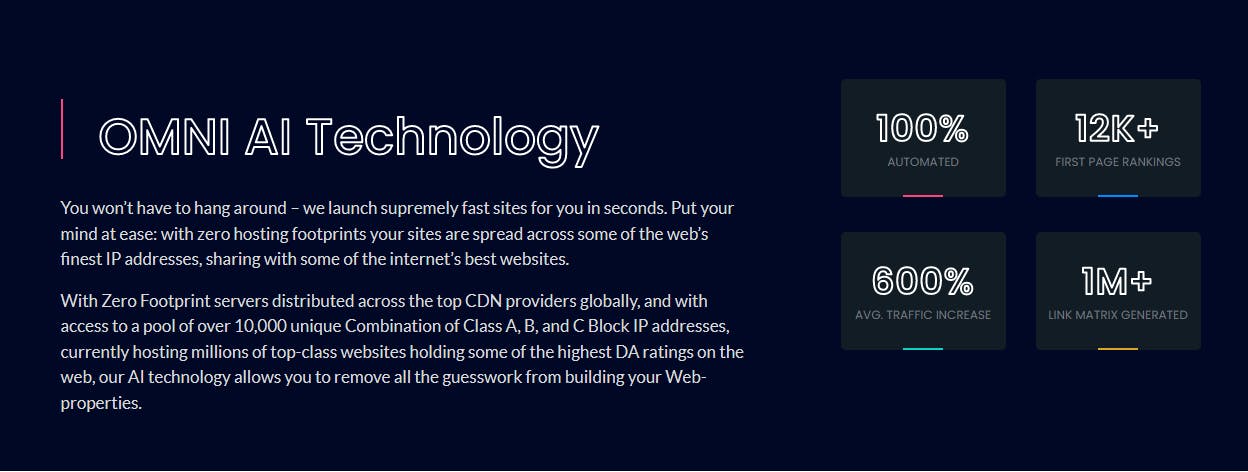
The answer changes depending where you look for information. The tagline you see when landing on the homepage reads: “Unleash Unlimited Traffic, 100% Automated [;] Undetectable, Untraceable, Unstoppable.”
It further goes on to describe features such as: “OMNI AI CRM,” an AI assisted platform for managing contacts & discerning their intent; “OMNI AI Matrix,” a tool to help you understand & manage your inbound & outbound link profile; and “OMNI AI Content,” a tool to generate web content on the fly using the keywords of your choice. That should set off anyone’s internet scam alarm.
Additionally, there are many mentions of website design & hosting throughout their offering, though this doesn’t have a dedicated product page:
Looking on the LinkedIn page of Manny Hernandez, Omni AI CEO, you may get a different impression:
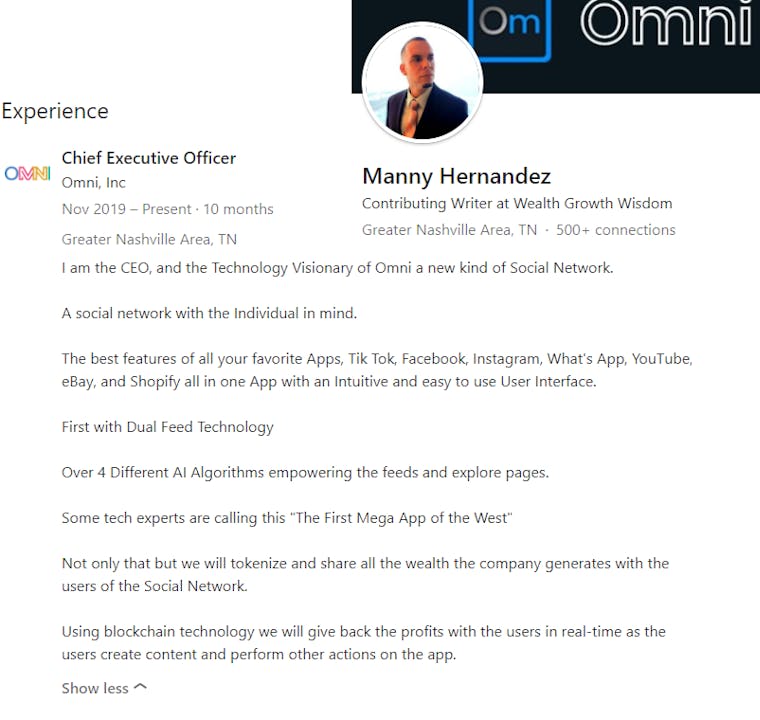
This description gives the impression that the site is a social network, and one which incentivizes user interaction as well.
This gives a very different description than what’s on the website, which paints it as a B2B product; at the very least, the site certainly doesn’t appear to be advertising a social network.
The conflicting information prompts us to dig deeper on the Omni AI executives, and get a better idea of their past business dealings.
4. Parsing Out the Complicated History of The Omni.ai Executives
The wealth of leads we have at this point gives us a lot to dig into, and almost everything points to one common denominator: a company which the Omni AI CEO Manny Hernandez started in 2014 called “Click Cash Marketing.” This includes a subsidiary called “Rock Solid Traffic,” which is accessible from the Click Cash Marketing Website.
Click Cash Marketing describes its services as follows: “Click Cash Marketing, Inc leverages our network of premium Email Publishers, Real Time Bidding Platforms, SMS Marketing Systems, Native Ads Networks and Retargeting Technology to deliver targeted advertising to qualified prospect’s across multiple verticals and English-speaking regions.”
From what can be discerned by using the website, the customers are usually seeking leads in the “make money from home” vertical. There are a lot of mentions of “Solo Ads,” or email-based advertisements you buy from other email list owners. They’re typically sent as dedicated emails, and the entire message is all about your promotion.
People buying traffic from the “Rock Solid Traffic” wing of Click Cash Marketing pay per-visitor for leads who are likely to convert.
4.1 Click Cash Marketing Officers Timeline
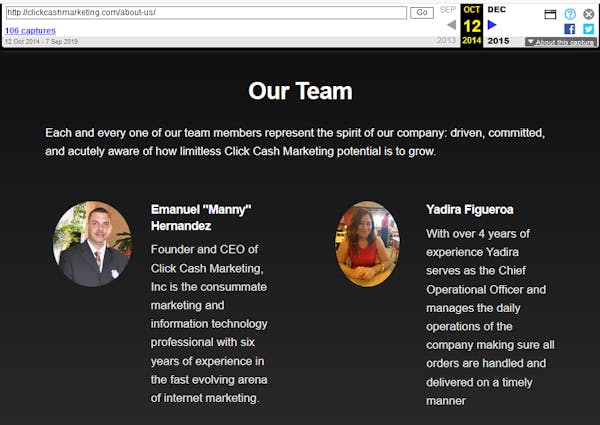
Q4 2014: Site starts becoming archived by the Wayback Machine
Officers:
- Manny Hernandez, CEO
- Yadira Figueroa, COO
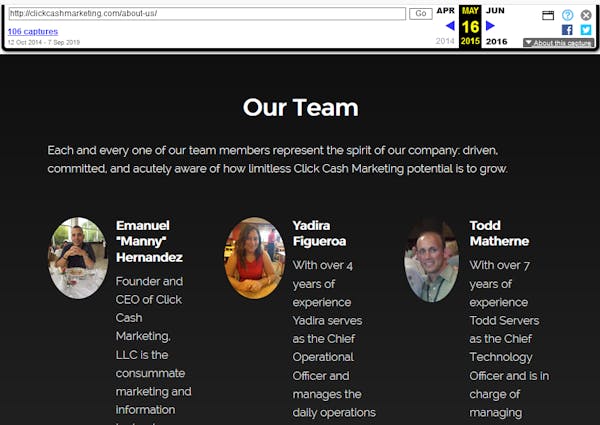
May 2015: Appearance of Todd Matherne as CTO
Officers:
- Manny Hernandez, CEO
- Yadira Figueroa, COO
- Todd Matherne, CTO
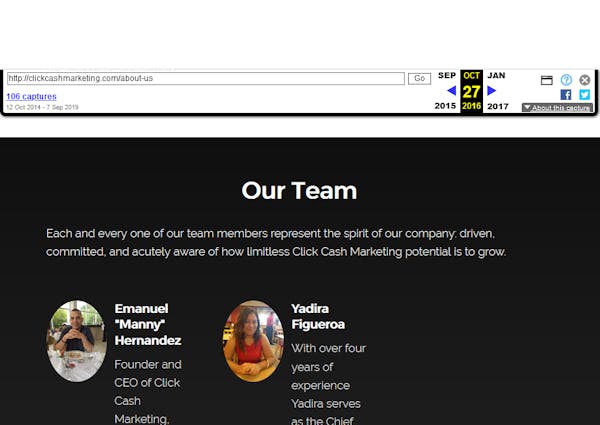
Oct 2016: Disappearance of Todd Matherne as CTO
Officers:
- Manny Hernandez, CEO
- Yadira Figueroa, COO
Aug 2017: Appearance of Almir Lukach as Head of Media Buying
Officers:
- Manny Hernandez, CEO
- Yadira Figueroa, COO
- Almir Lukach, Head of Media Buying
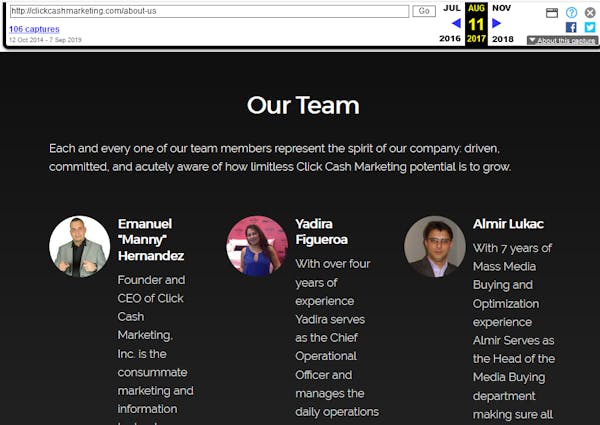
With all this information, we are now 100% sure there is an established relationship of many years between the registrants of domains in the Omni Redirection Network.
4.2 The CEO’s History of Traffic Manipulation & Suspicious Activity
4.2.1 Prior to Click Cash Marketing
Before starting Click Cash Marketing, Manny seems to have been extremely active in the world of blackhat SEO/marketing.
His Youtube channel is still chock-full of guides on how to leverage his custom tools which exist in a questionable ethical space.
Many of his first videos relate to a tool called “Traffik Buster,” self described as: “the best Traffik Generationg Sofware on the market.”
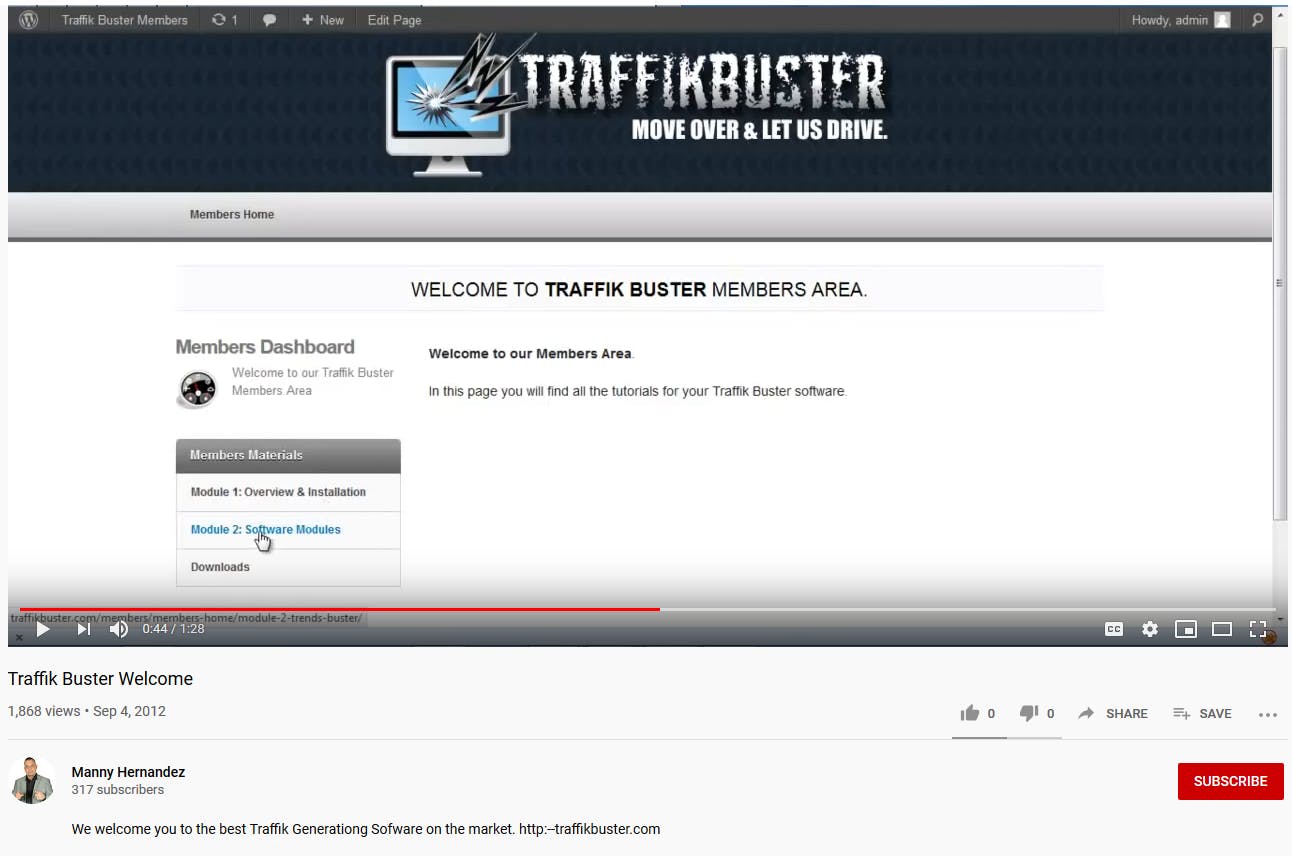
The tool is used to rapidly tweet from a variety of accounts, and could perform a variety of functions such as: proxy IP rotation, post timing, GEO specific trend analysis, and a variety of other tools to help people amplify traffic to their “money domains” (domains where a user completes a CTA and the affiliate then gets paid).
Such a tool would almost certainly violate Twitter’s Spamming & Misleading Links policies (among others).
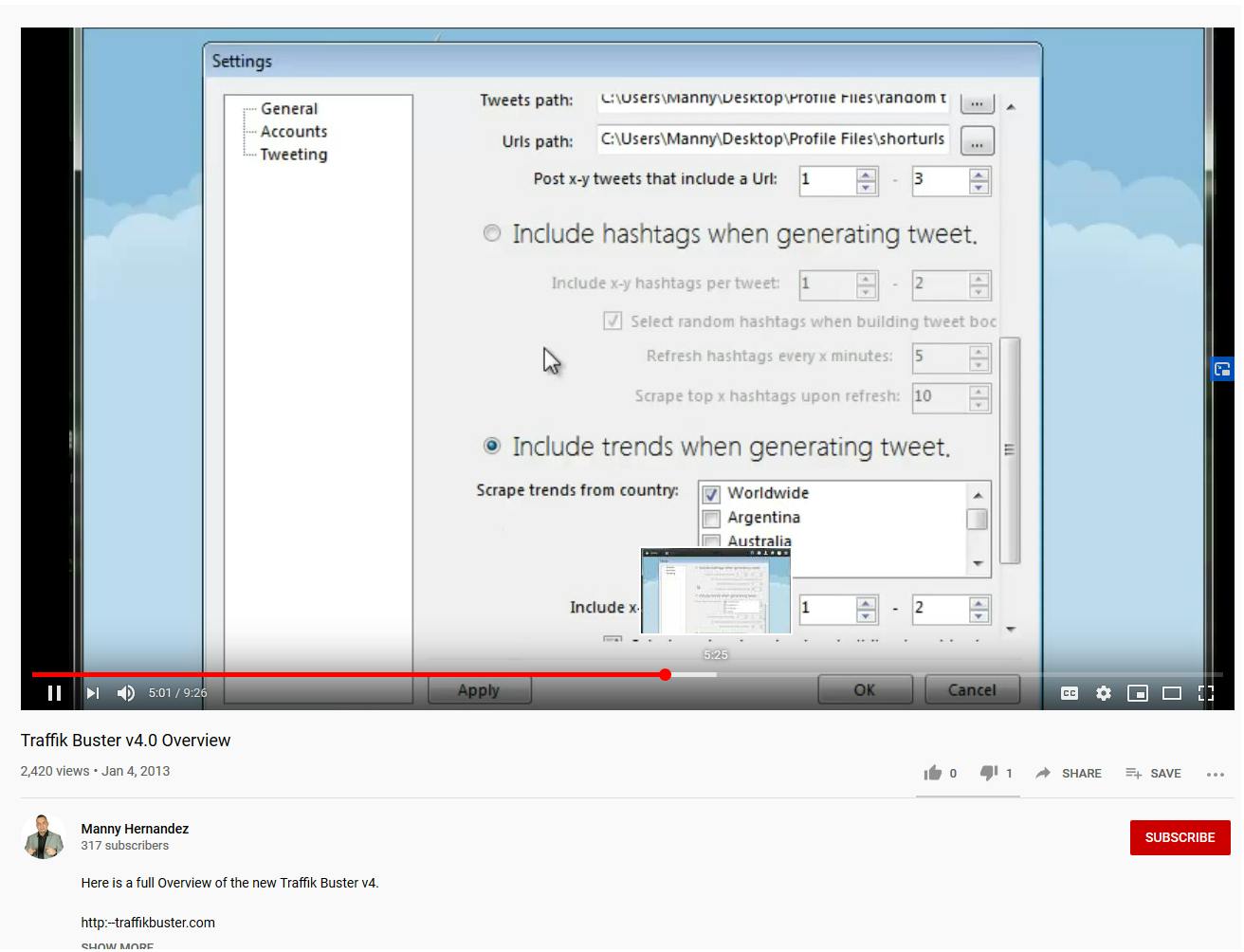
He continues to work on & support Traffik Buster up until version 4 (released in 2013), at which point he posts an interesting video titled “Traffik Buster Cloaking Script Tutorial.”
In this video he shows off a script that is meant to be uploaded to a throwaway domain, and intelligently redirects users to “money domains” without sending bots / undesirables to the same place.
He says “”Twitter is notorious for banning a domain that is being posted several times from several accounts in a short period of time, so to protect your domains, or to keep promoting domains that are actually banned already, we use the cloaking script. That way, you can upload this to a throwaway domain, that you don’t care if it gets banned, and you can keep promoting the domain that you like.”
Here’s an example:
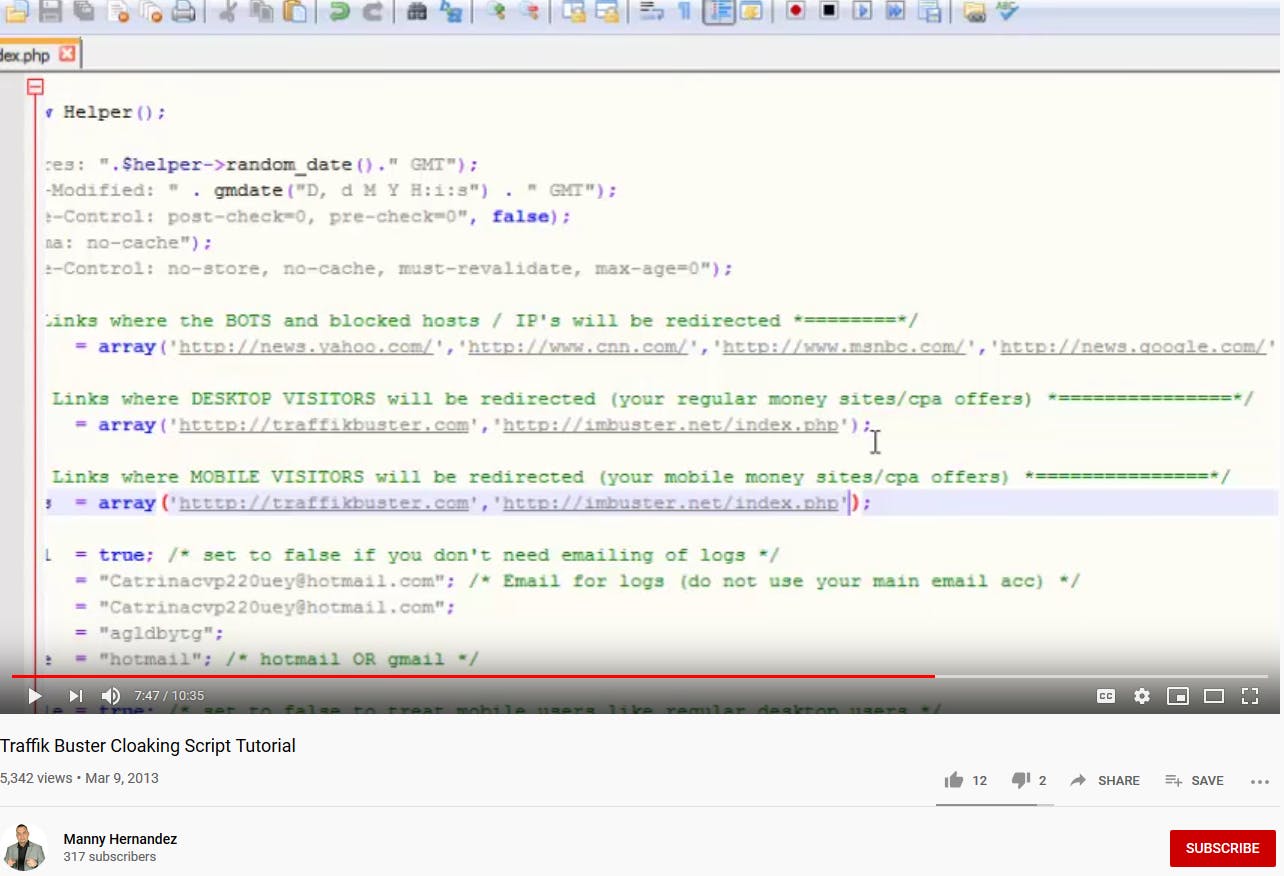
It is at this point where we were reminded of the profile of the Omni Redirector Network; it’s likely that we are currently being sent to the list of domains in the “Links where the BOTS and blocked hosts / IP’s will be redirected” section of a script very similar to this.
Some of the destinations are even the same now as they were in 2013 when the video was recorded. As of the time of writing, even residential IPs from a variety of locations are sent to the same list that we have provided in earlier sections.
It seems likely that these 12,000+ domains are throwaway domains which are meant to amplify the CPA campaigns’ of his clients / subscribers.
Omni’s website has been under construction until recently, and it may be that we are the precipice of Social Media manipulation using the new evolution of his traffic cloaking script.
4.2.2 Allegations of Fake Leads and DDoS Attacks
Much information in this section is subjective, and can be traced to to a moderator at a small traffic marketplace called Udimi.
They wrote a blog called “Story of a Scam Manny Hernandez,” which details how the traffic Manny sold through Udimi came to be under scrutiny, and eventually resulted in his banishment from that platform. Such claims also led to him being banned from at least 2 other solo ads marketplaces.
Much of the evidence to support these claims was posted to marketing Facebook groups between 2014-2015, and much of the original evidence is no longer accessible. For these reasons, we are choosing not to speculate too much in this section.
Suffice it to say: there are many unhappy past customers, and several who claim that Manny crippled their websites / servers with DDoS attacks in retaliation to their complaints.
That being said, the writer of the linked blog clearly has a chip on their shoulders from interactions with Manny, and did a decent job of documenting messages between the quarreling parties.
4.2.3 FCC Citation for Sending Telemarketing Text Messages to Numbers on the Do-Not-Call Registry
In December of 2018, Manny is issued a citation for spam texts to phone numbers on the Do-Not-Call registry. According to the citation: “Hernandez’s texts were sent for the purpose of encouraging people to purchase membership into MLM businesses and other get-rich-quick schemes.”
It is maybe also worth pointing out that, after leaving Click Cash Marketing in 2016, Todd Matherne worked on a tool called “ExtremeSMS.” Matherne describes his inspiration in the following passage from this article:
“[H]e realized that these complex [spam] filters were making it nearly impossible to send marketing text messages to a large number of people, limiting the number of leads he could generate. None of the text message apps on the market could get past these unique filters set by mobile carriers, so in true entrepreneurial fashion, Matherne developed his own app: ExtremeSMS.
‘ExtremeSMS virtually guarantees text messages will be read by circumventing obstructionist filters,‘ he said. ‘It’s completely TCPA-compliant and currently the lowest cost in the industry.'”
On the face of it, it sounds like there is no way that this could have ever been legal. It makes one wonder: is there a shared culture of casually discarding consumer privacy in favor of making a quick buck between Todd and Manny? Is that shared by their current project, Omni AI?
5. Present Day – The Return of Rock Solid Traffic and the Introduction of Omni
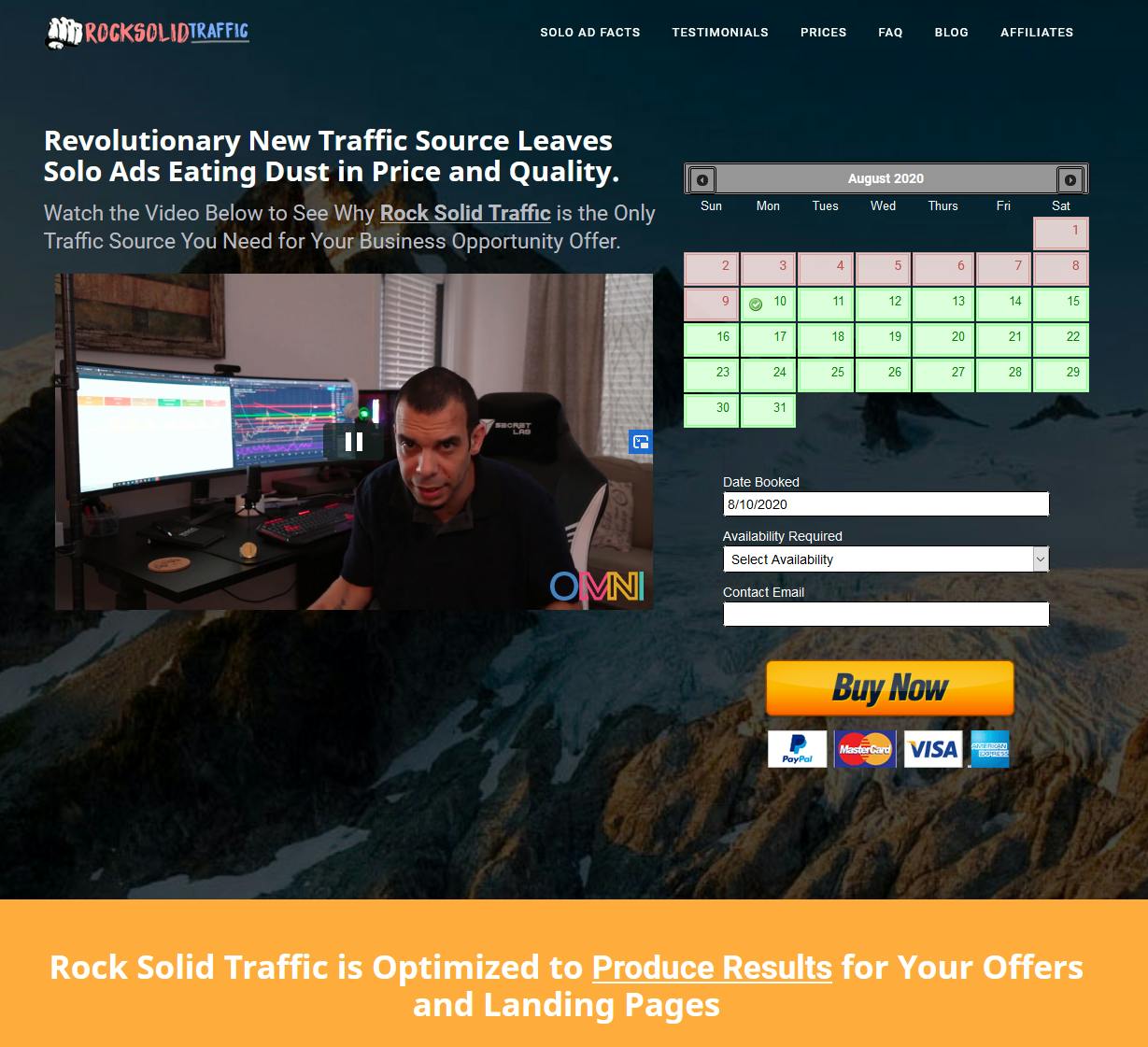
Leading up to the FCC citation, and for a period following it, the “Rock Solid Traffic” portion of the Click Cash Marketing site was not functional. As of the past few weeks, it has returned with a new “OMNI” logo (visible in the above image).
A video accompanies the page’s return, and in it Manny offers an emphatic explanation for the site’s disappearance: “we were making more money using the traffic than selling the traffic.”
He continues: “we have been building technologies for you to thrive in the space, […] when you buy traffic for the first time you’re going to get your own Omni tracker, […] our own in house built tracking technology.”
This tracker is meant to work across all mediums, and all platforms. He says “you can track all your campaigns all your marketing needs under one roof 100% free when you place your first order here with rock solid traffic.”
This made us think back to “omnitrack.click,” the canonical domain shared by these many individual redirectors.
There is some concern that redirection would happen in a much higher volume if this tracking tag was appended to many creatives across many platforms. It could be that Omni’s aim this time around is to provide people with the tracker, and piggyback that on many different types of creatives. All this in order to create traffic which could then be attributed to many unique users.
As we mentioned in the introduction: Redirects can easily be used to manipulate web traffic rankings. Even users who immediately bounce may influence certain ranking systems
Takeaways & Next Steps
1. The redirect behaviors that we observe today are very reminiscent of Omni CEO Manny Hernandez’s previous traffic generation scheme “Traffik Buster”
- As part of that scheme, throwaway domains host a script which intelligently redirects valuable users to a different sites than those who would audit the links. It was designed that way so that users could link to sites which would be banned by the platforms on which the links are posted, such as Twitter.
- Given that Manny now describes Omni AI as a way to enjoy all of your social media platforms, it may be possible that the scope of Traffik Buster has grown beyond Twitter, and now is capable of exploiting additional social media platforms.
- Social Media platforms should take extra care to suppress posts which contain any of the Omni Redirector domains, as those posts are likely to take users to unsafe locations
- Publishers which are destinations of these bouncers should check their data to make sure there are not too many events where the HTTP referer header is in the list of known Omni Redirector domains
2. Omni AI is distributing tracking tags for free as part of the return of Rock Solid Traffic
- In general, ad buying platforms should be wary of third party tracking tags the first time they are observed (at least)
- It may be necessary to strip tracking tags which match the domains on the Omni Redirector Domain list. There is a potential that these tags will force navigation events on users
3. Omni AI appears to still be in its formative stages, and things may change quickly
- Keep your block lists up to date, and don’t go too long without making an update.
- You can use the deepsee.io advanced search to fetch a fresh list of newly registered sites with high redirector risk every so often.
- If anything significant changes, we will post an update.










