Affiliate marketing programs reward publishers for sending users to merchant sites. When those users end up making a purchase, the merchant / brand generally pays a commission to the affiliate network, who compensates the publisher based on the terms of their operating agreement.
Sometimes the publisher gets a transparent % of the commission, other times the network offers alternative methods of compensation, like CPC (cost-per-click).
In this article, we will examine how affiliate fraud is perpetrated using cheaply purchased pop-traffic from adult / torrent sites.
How do Merchants & Affiliate Networks Know Who to Pay?
Merchants determine who is responsible for bringing a user to their site based on the historical browsing activity of that user. When a user arrives at an e-commerce site, the parameters in the url query string often include information about the campaign / affiliate network that brought the user in, for example:
<http://www.skechers.com/?utm_source=affiliate_abc&utm_medium=cse&szredirectid=16129412645202301917910090301008005&CAWELAID=120015390001338230>
In the above example, the utm_source alerts us that the user arrived at sketchers.com by means of an affiliate link from the affiliate_abc affiliate network. The retailer would then log that relevant information, cookie the user so that they can fetch this info if they ever come back, and the affiliate network would get a commission if this user ended up purchasing.
Taking another step back, we can see how the retailer & the affiliate network might align their records. Let’s take the request which ended up redirecting us to sketchers as an example:
<https://redirect.affiliateabc .net/rd2?mid=27754&dMid=27754&tokenId=18P&bId=314&bidType=11&af_id=615103&af_rid=null&af_permalink_id=20dff412e572a94749039045eb4ea07a52305518&cobrand=1&af_placement_id=4341223&afCampaignId=kkz3l0abt302l1pj0mg90&rf_code=af1&af_assettype_id=14&af_creative_id=2913&t=http://www.skechers.com?utm_source=affiliate_abc &utm_medium=cse&szredirectid=16129412645202301917910090301008005&CAWELAID=120015390001338230&br=16129412647298893945602020301008418&rf=af1&vsc=dau&rdrSerial=b1854329-231d-40db-95c4-2bfefba89f86&redirectId=16129412645202301917910090301008005>
It seems like the 2 requests can be correlated by their redirectid (16129412645202301917910090301008005 in this case), and this allows the affiliate network to associate the event to any number of other parameters like: af_id (affiliate ID), af_placement_id (placement ID), afCampaignId and more!
Now Sketchers & the affiliate network speak the same language; Sketchers can say: “hey affiliate, the user who arrived by redirectid 16129412645202301917910090301008005 ended up buying $200 worth of goods! Here’s your cut!” Realistically, this all happens programmatically, but you get the idea.
Not every affiliate uses these parameters, or passes data this exact way, but the principles are the same: the merchant cookies the user with information about how they arrived at the site, and that stored information is used to notify & compensate the affiliate network in the case of a later purchase.
Cookie Stuffing Explained
Cookie stuffing is the practice of forcibly navigating users to a retailer site, causing cookies to be dropped on users with the fraudster’s affiliate information. This is done for the express purpose of claiming affiliate revenue if that user ever completes a purchase at the retailer associated with the forged cookie.
One of the most famous cases of cookie stuffing involves eBay, and a company called Digital Point Solutions (DPS). In 2006, eBay started worked with the FBI to put its most prolific affiliate, DPS, behind bars.
Their research showed that display ads served by DPS contained hidden redirects to eBay, which caused cookies to drop with DPS’ affiliate code. Digital Point Solutions also is alleged to have used browser extensions to secretly load eBay in invisible frames, causing users to be cookied with DPS’ affiliate info.
As the linked article points out: “So many random users were carrying their cookies that some of them inevitably ended up on eBay.”
Cookie stuffing is truly a numbers game; be where the people are, cookie as many as you can, and just wait for them to make a purchase at a major retailer.
In response to Digital Point Solutions’ cookie stuffing attempts, eBay ended up setting a trap: they hid an invisible image on their home page that wouldn’t load for users who bounce instantly, and they logged users who were served the image. They could then deduce that users who had cookies, but had never been served the image, were cookied by fraudulent means; those users had never even been to eBay, or they hadn’t spent enough time there to be served the image.
According to eBay’s civil complaint against Digital Point Solutions’ CEO (page 17), 650k cookies were stuffed by the malicious browser extensions & bogus ads over the course of the ~11 day test in June 2007. Business Insider reported that DPS made ~$1.1 to $1.5 million per month from eBay.
We can use that info to estimate that they made between $400k and $550k with those 650k cookies, or between $.62 and $.85 per-cookie.
Is this “invisible gif” that eBay leveraged still an effective solution? It would likely still work to thwart drive-by cookie stuffing with immediate bounces, but fraudsters are always at the cutting edge of detection. Luckily, the fraud detection tools have also improved since then.
With the arrival of viewability tech on the scene, the good-guys could likely detect cases where eBay was loaded in an invisible frame, or behind display ad content, like DPS did a couple decades ago.
However, our research here will show how trivially easy it is to send a user to retailer pages using pop-traffic & affiliate redirect links. Users arriving at retailers this way might not even realize it, and could therefore leave the page open for quite some time; they also end up loading the retailer page in a way that wouldn’t trigger fraud signals from a viewability check.
Fundamentals of a Pop’n’Stuff Scheme
“Be where the people are, cookie as many as you can, and just wait for them to make a purchase at a major retailer.”
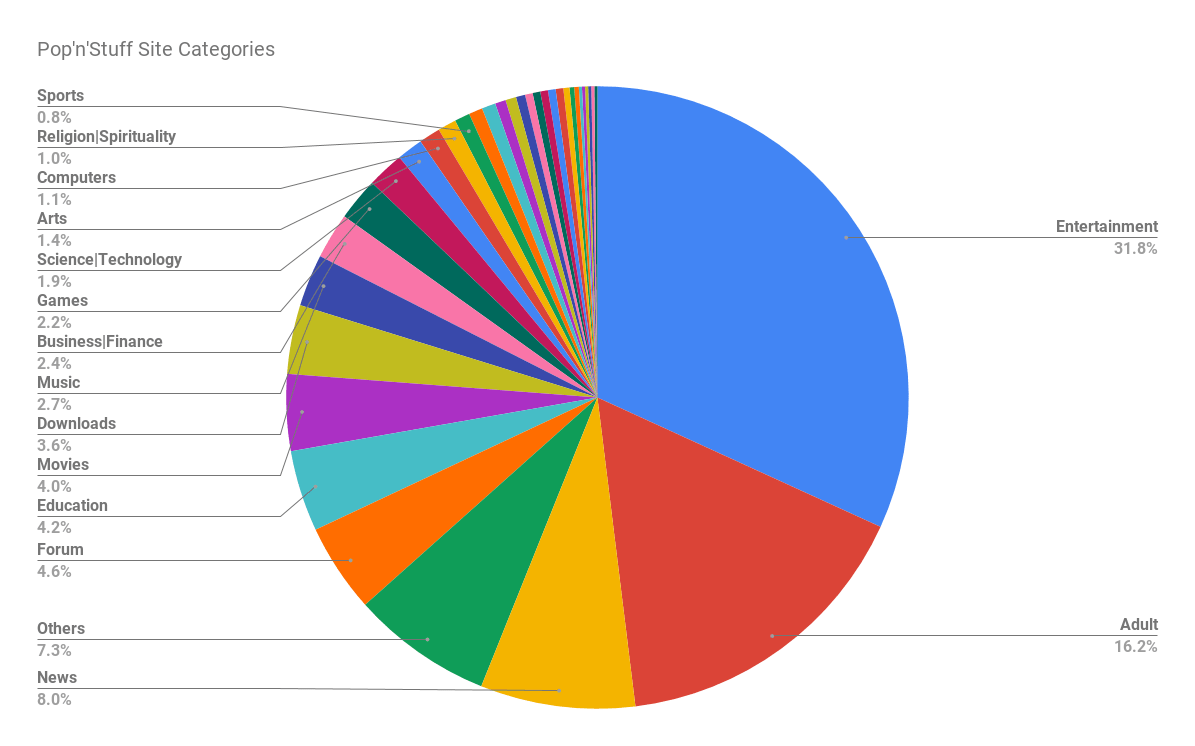
We’ve been tracking an affiliate fraud scheme which leverages pop-unders to send users to 60+ retailer pages since February began. For fraudsters, the beauty of such a scheme is that they can reach users where premium advertisers can’t: illegal streaming sites, torrent trackers, adult sites, and other categories of site that premium ad networks don’t usually go for.
This chart shows the category breakdown of sites in the pop-under redirect network we have been tracking, titled “Pop’n’Stuff” for the purposes of this blog post.
Here’s an example of what the user experience is like for a visitor to an adult site who is part of the Pop’n’Stuff network:
Lets slow down the redirect portion of the video to get a more clear look at how we get from p.netund.com, an ad serving / traffic routing domain belonging to PopCash, to samsclub.com:
Did you notice the redirect to gamebrilliant.com? This is a content domain that the Pop’n’stuff network uses to hide the true origin of traffic. Don’t worry about missing something though, we’re about to break down the redirect pattern in great detail.
The initial PopCash popunder redirects users through a tracking link that also determines where they will be sent next. For example:
https://trk.blmte.com/click.php?key=p08l0438b5ahkk84vl54&clickid=92556061482&bid=0.00028&siteid=402389&category=Adult&cc=US&operatingsystem=Windows&campaignid=311776&connection=WiFi&device=desktop&browser=Chrome&carrier=
This tracking / redirect link relates to binom.org, a tool which helps their users effectively rotate & manage redirect links for their affiliate campaigns:
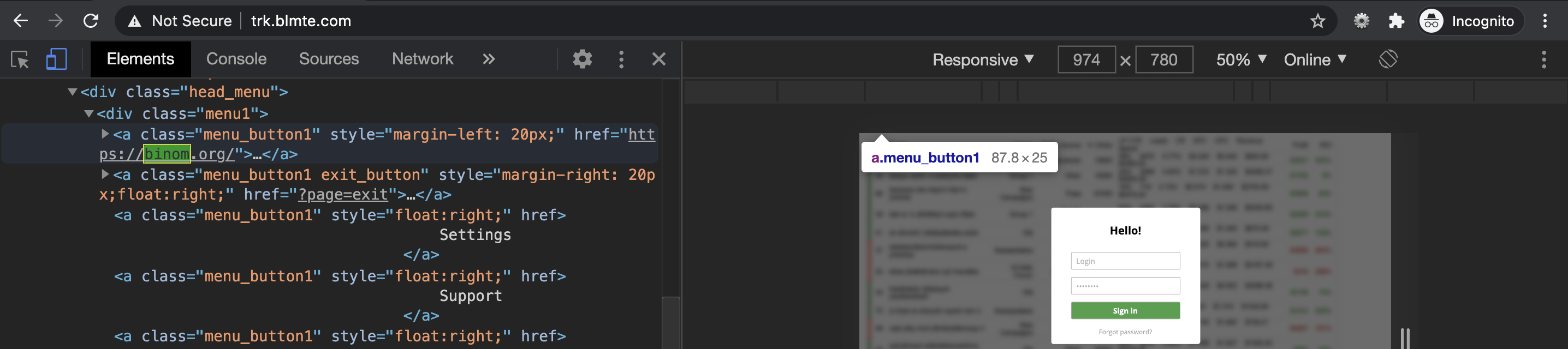
After the fraudster logs the true source of traffic here, users are redirected to a rotating cast of content domains used to hide the true source of traffic, including gamebrilliant.com.
Those links are formed like:
https://www.gamebrilliant.com/1.php?url=https://r.srvtrck.com/v1/redirect?type=linkId&id=db6dcb170fd44f9fb894260ab0484ec5&api_key=2fe47058ccdf28a42879b9ff7dfa613c&site_id=be736ee3da754e79b57f447baf29a08f&dch=feed&ad_t=advertiser&yk_tag={clickId}&referer=https://www.gamebrilliant.com/banner.php
The url we will next be forwarded to is in the url parameter, and is a redirect link from r.srvtrck.com, and then usual next destination is yet another redirect url, go.lnknam.com. For example:
https://go.lnkam.com/link/r?u=http%3A%2F%2Fwww.samsclub.com&campaign_id=wpREBC9CVDeQsr81u1sMGy&zsb=v0304000118844476585ab9e945208a911cbf940254e2&source=be736ee3da754e79b57f447baf29a08f
That link generally takes users to a script hosted on v6ur9n22r9.execute-api.us-east-1.amazonaws.com, which forwards them to their ultimate destination. For example:
https://v6ur9n22r9.execute-api.us-east-1.amazonaws.com/production?u=http%3A%2F%2Fwww.samsclub.com&key=19979e1a3ce3d1fac91e43416a7c350f&cuid=dNRbuqFjsGj9EvtsZLFZ7B&subId=22bxq7
Once we make it to lnknam.com in the referral chain, the ultimate destination is clear (samsclub.com in this case).
That’s a lot of redirects! To make understanding this chain of events a little more simple, and to give better insight to the affiliate domains we see most associated, we have created a flowchart showing the most observed redirect patterns created by sites in the Pop’n’Stuff network.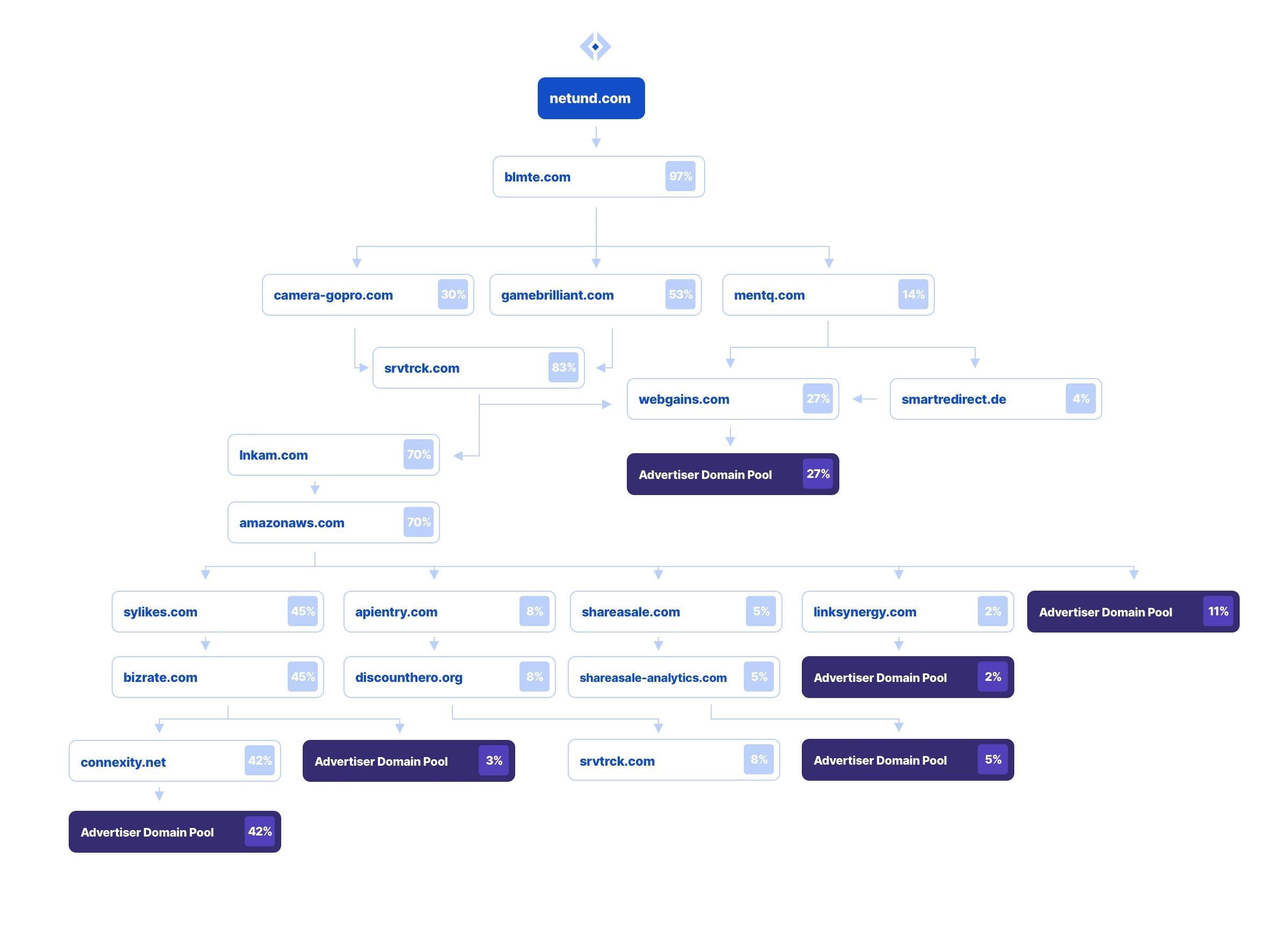
This was based on analysis we performed of the Pop’n’Stuff affiliate fraud network between Feb 1st and Feb 19th; due to the dynamic nature of the redirect scheme, this image is likely to become stale over time, but I think it’s still useful for the purposes of highlighting how complex the chain of events often is when it comes to affiliate fraud. For the purpose of a clean image, we excluded some paths which appeared very sparingly. Pop traffic resulting in cookies stuffing is not limited to any one platform, it’s likely to affect every player, big & small alike.
Information for Brands Affected
In the above image, the “Advertiser Domain Pool” refers to 60+ retailer pages we identified as destinations of traffic from this affiliate fraud scheme between Feb 1st and Feb 19th 2021. Those domains are in the “Brands Affected” tab of the research we are linking here, and also, for ease of searching, in the following code block:
nike.com, macys.com, wayfair.com, globaldelight.com, canadavetexpress.com, bhphotovideo.com, modlily.com, clocksandcolours.com, build.com, partsgeek.com, touchofclass.com, groupon.com, rotita.com, epson.com, haband.com, buymbs.com, thumbtack.com, zgallerie.com, plainjane.com, transunion.com, pureformulas.com, brownells.com, thenorthface.com, katom.com, grenade.com, sephora.com, northerntool.com, maurices.com, paessler.com, amazon.com, blair.com, lifeextension.com, manhattanhomedesign.com, thredup.com, xcaret.com, birkenstock.com, lilicloth.com, soccer.com, softsurroundings.com, nordstromrack.com, jmclaughlin.com, myinnovo.com, petco.com, springhillnursery.com, webstaurantstore.com, carparts.com, purple.com, lampsplus.com, canadapetcare.com, samsclub.com, ssense.com, tomrockets.com, orthofeet.com, vitalydesign.com, grandinroad.com, skechers.com, modcloth.com, kohls.com, zennioptical.com, liverpoolfc.com, anniecloth.com, justfashionnow.com, noracora.com, stylewe.com
The domains we crawled to get these results are in the “Crawl Domains” tab, though this list is constantly expanding; really, any publisher working with a pop-traffic vendor could be the source of this activity.
In addition to just highlighting the brands affected, we are making available for those retailers a selection of query string parameters we detected when a Pop’n’Stuff users arrived on their site (in the “Query String Parameters” tab). For example:
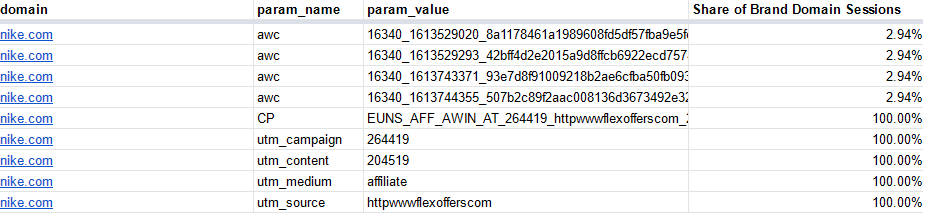 The “domain” in this case is the retailer domain; the “param_name” is extracted from the landing page url, as well as the corresponding value. The “Share of Brand Domain Sessions” represents what % of the time this value appeared in Pop’n’Stuff crawls where we arrived at the retailer in the “domain” column.
The “domain” in this case is the retailer domain; the “param_name” is extracted from the landing page url, as well as the corresponding value. The “Share of Brand Domain Sessions” represents what % of the time this value appeared in Pop’n’Stuff crawls where we arrived at the retailer in the “domain” column.
The same level of information is available for all the intermediaries / platforms involved. If you are a representative of a mentioned affiliate platform who is interested in this information, please reach out to us at [email protected].
Conclusions
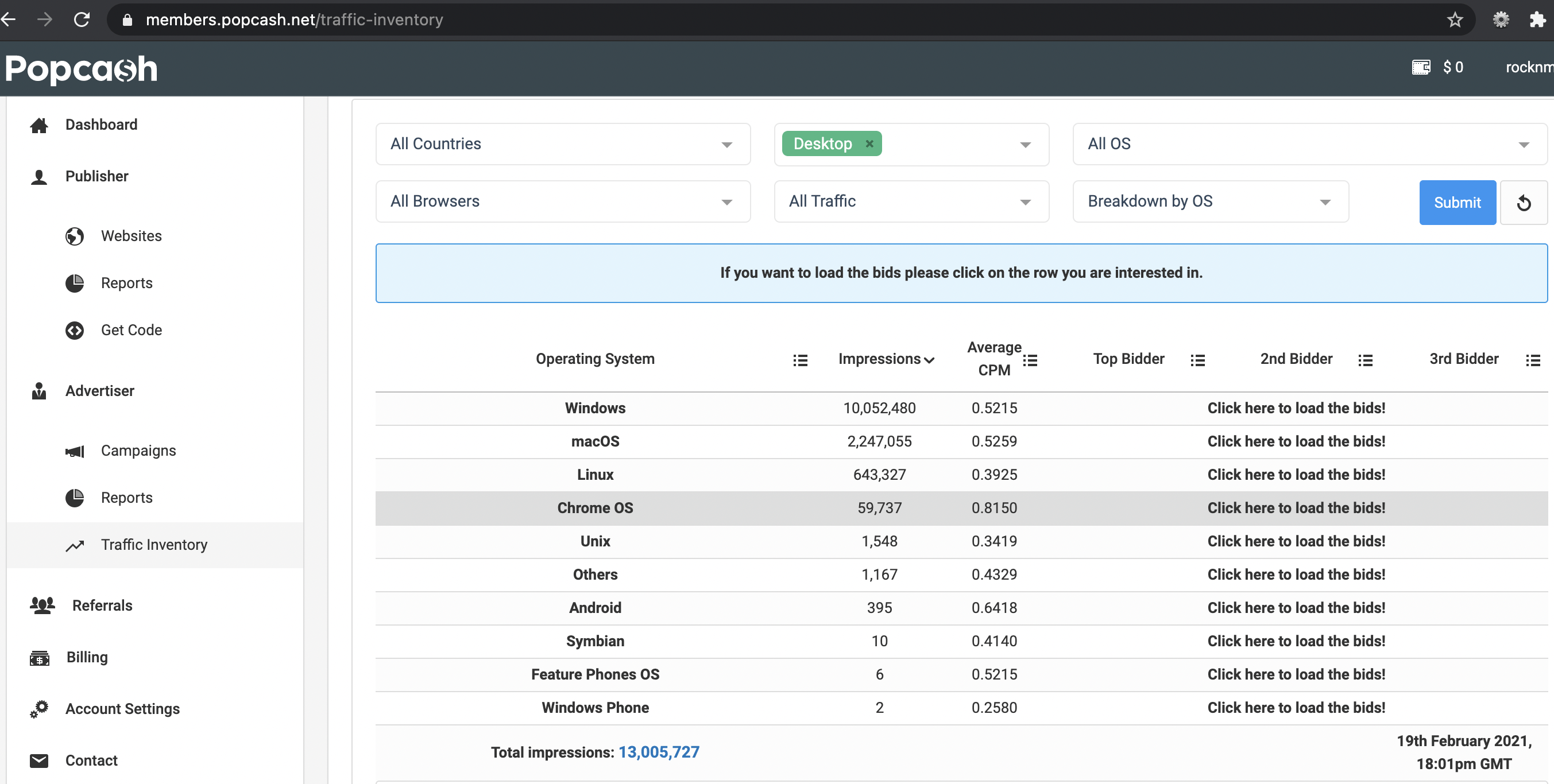
This image shows that you can get 1000 pops from 1000 unique users for about 52 cents as an advertiser using PopCash’s network (pop traffic generally only triggers once per-unique). That results in 1000 unique cookies being stuffed on users, linked to a variety of retailers.
If we put that in context with the DPS / eBay cookie stuffing revenue, they made an average revenue of 62 – 85 cents per-cookie stuffed. Granted, cookie retention rates are probably much worse now than they were in the 2000’s, but even if a scheme like Pop’n’Stuff is 1/1000th as profitable, the fraudster would make money.
Affiliate fraud is a more passive kind of exploit, that nevertheless affects retailers’ bottom lines. We are in a unique position to be able to alert brands & affiliate networks of this kind of activity, because we interact with pages like a user does, and we trigger these hidden pop-up and redirect behaviors.
Without this measurement context, it would simply not be possible to connect a user arriving at a retailer page with a popup that triggered on a porn/torrent site.
if you are a brand looking for real time updates when we detect affiliate fraud connected to your site, please reach out to us by e-mail at: [email protected]