Introduction
As an ad-fraud researcher of a decade now (that’s crazy to type), I consider myself something of an expert when it comes to identifying the places where real humans are weaponized to create invalid ad impressions. Knowing where to look is half the battle, as anyone who runs a business built on crawler data will tell you. DeepSee.io’s automated investigations into recently [re-]registered sites & the long tail of the web consume thousands of device hours of each month, and the threat actors we find are ephemeral; it’s often impossible to assign a responsible legal entity to the schemes we find. As such, the best we can often do is alert our partners to the risk associated with certain seller IDs, or domains, and move on.
Luckily for you, our reader, this is not one of those times. Today we’re documenting an enormous scheme that’s been running for years, and what’s more: this is something you might easily discover for yourself using tools you may already have at your disposal. There’s one more thing that’s a major outlier in this case: a remarkable lack of care when it comes to hiding who is behind the curtain. Only one thing is not for certain: given the sellers, managers, and re-sellers that we present as potentially involved, what is their SOV in the bid stream over months / years, as it relates to this scheme.
In this post we will share some educated guesses based on publicly available data, and logs you & others may choose to volunteer. First things first, watch the video. I recommend watching it at full screen, and at a high resolution, as it walks you through some datasets that will hard to see at low resolution, and which will be included at the end of this post. Jump down there first if you want to follow along with the data sheet!
Aspects of this post may not make sense if you haven’t watched the video yet, so it’s highly recommended to watch the video.
To summarize its contents:
- We identified a piracy site ranked in the top 100 most-visited by SimilarWeb (zonatmo[.]com)
- We identified a roster of “clean” content sites used to launder the traffic of visitors to this piracy directory
- These sites generated a collective 1 billion+ page views in November 2024, per-SimilarWeb
- Both the pirate site & the laundering fronts appear to be owned and/or managed by Nakamas Web SL
- A google search makes clear who owns / founded Nakamas Web SL
- Using the included visitation data in the companion worksheet, we hypothesize an extremely conservative ad spend of 200k/month in November. The true number could easily be 10x that amount.
Introducing the Players
When we talk about piracy that’s supported by programmatic display / videos ads, we’re often talking about traffic laundering. In a laundering scheme, there are two classes of domains involved:
- Directories: when you type in something like “watch free movies,” or “read manga online,” chances are you’ll be taken to a directory. These are sites that connect you to the pirated content you’d like to consume. They are often easy to find using search (by necessity; they have to change domain names often), and this ease in locating them also makes it hard to gain access to premium exchanges / demand (these sites usually appear on industry standard piracy lists).
- Most common on-site monetization strategies: native ads (CPC), popunders (CPV).
- Laundering fronts: these appear as “clean” when you visit them directly, but are usually actively managed by the folks behind the directories. They have hidden behaviors that only present themselves if you visit via some prescribed source (the directory). These sites are often able, for at least a short time, to monetize using CPM based ad products such as display / video / audio ads.
- Check out another in-depth investigation of ours on this very subject: https://deepsee.io/blog/a-case-study-in-monetizing-piracy#3-introducing-the-players-amp-explaining-the-evidence
Tu Manga Online: The Piracy Directory

Tu Manga Online (aka TMO) is a pirate site directory catering to Spanish speaking audiences who seek free copyrighted comics. Like most pirate directories, the domain rotates fairly often, and the domains in use since 2023 are as follows:
| Domain | Notes | Best Tranco Rank | Best Rank Month | Best Rank in Dec 2024 |
| tmofans.com | Redirects to zonatmo | 821,732 | 1/1/2023 | 3,160,640 |
| lectortmo.com | Redirects to zonatmo | 1,506 | 9/1/2023 | 346,423 |
| lectormanga.com | Still active | 9,132 | 2/1/2024 | 21,660 |
| visortmo.com | Redirects to zonatmo | 1,495 | 4/1/2024 | 4,145 |
| zonatmo.com | Active | 1,518 | 11/1/2024 | 1,544 |
As our video shows, the current iteration (zonatmo) has an enormous number of recent visits. Below is a screenshot of their 3 month traffic trends in SimilarWeb; you’ll notice it shoots up from almost nothing to over 500M visits:

This trend is echoed by their Tranco Rank, which shows it as unranked in August, barely ranked in September, and enormously popular in October & beyond:

As the video shows, when you click to consume content on the directory, you’re sent to a laundering front.
It is important to this investigation to note that the privacy policy and terms pages for the directory site, zonatmo as it stands now, will take the reader off-site to the Nakamas Web site (nakamasweb.com/policy.html). This might seem like something insignificant, until combined with the information in our next section.
Nakamas Web SL: Laundering Fronts
Over the scheme’s lifetime, we have observed 112 laundering domains used. There tend to be 1-2 dozen active at a time. In 2024, we saw about 60 of these sites peaked in popularity, but this didn’t happen all at the same time. Let’s look at this chart which shows how many appear in the Tranco top 100k, and 500k, each month:

As we can see, the peak # of domains we saw in the top 100k was 24, and that was in October. The full list of laundering fronts is made available in the supplementary data packet, located at the end of this post.
In addition to sharing 100% of their 15k+ line ads.txt files with each other (a deterministic signal of relatedness @ a business level), many of the sites feature a snippet like this in their privacy / terms pages which denotes Nakamas Web SL as the responsible entity:

That is the exact same site which hosts the privacy policy for our directory site, zonatmo. This deterministic connection is a bit of a formality, because the hidden functionality that we demonstrated in the video at the top of this post is simply not possible without cooperation between directory & laundering site. Using this little text snippet, it becomes easy to find a whole bunch of the laundering fronts, as exemplified below:

There’s actually an even easier way to identify all the laundering fronts, as I’ll demonstrate in the section below which covers supply chain transparency dataset (ads.txt &sellers.json) signals.
Who is Bringing This Junk to Market?

We’ve identified the responsible entity across both the piracy directory & our laundering fronts is Nakamas Web SL, but that’s only one part of the problem. Clearly Nakamas Web has found a roster of managers / sales houses / resellers who don’t look too closely at the quality of the inventory they bring to buyers, and thus they’ve had luck laundering their traffic for years.
Some info can be learned from actually going to these sites and looking at the logos / AdChoices pages attached to the ad units. Looking above, we can see an abundance of ad units with the Infolinks and Netpub logos (color coded by ad system), but that hasn’t always been the case; the makeup of sellers / managers has changed over the several years this scheme has been running. At a high level, it appears the site operators have had to adapt every few months, or every year at least, in order to find a new roster of sellers who don’t know/care about the way their traffic is sourced.
There’s a lot that we’ve learned by analyzing the header bidding technologies in use, parsing bid requests/responses, and going deep into their ads.txt declarations & the corresponding entries in sellers.json files, but that won’t tell the whole story. The truth of the matter lives in log files across many unique advertisers, DSPs, SSPs, and other such supply chain participants. Gathering a guaranteed representative sample of such log data is a herculean (or maybe sisyphean) task, and we won’t let it hold the release of this research.
Ultimately, this truth is only going to come out if enough people read this article, get pissed off, and subsequently decide to share details with each other. The truth could also come out if legal action ever gets brought against the entities involved (exceedingly rare in this industry), but maybe it can happen this time, given that we’ve identified a beneficial owner.
Useful Supply Chain Signals from Ads.txt and Sellers.json
This isn’t an ads.txt explainer post, so I’m going to gloss over a lot of things here that take for granted you understand the spec. For those seeking a refresher, check our blog post, or DigiDay’s explainer!
First off, the ads.txt files hosted by these laundering fronts are full of noise; at time of writing they are over 20k rows long as pasted into a text editor, but over 9000 of those rows are duplicates. What’s more, the files are full of lines denoting inactive supply paths, and paths which are not confirmed by the corresponding sellers.json files. As such, we have gone to great lengths to remove the noise from these files, and identify trends worth noting.
Adsystems Authorizing Specifically by Content Domain, or Mentioning Nakamas Web SL by Name
One approach we took was to identify sellers.json files which name Nakamas Web SL specifically, or denoted one of their sites in the “domain” filed of the seller object (the full result set is in the “Adsystems Authorizing By Name – Historic” tab of the companion data sheet, available at the end of this post). When we did this, we found that 10 ad systems mentioned 20+ Nakamas domains specifically in their sellers.json files, and had at least 1 authorization which was current. Those were:
| Ad System | Unique Seller IDs | Unique Nakamas Domains Listed | Unique Names Associated | First Authorization Observed | Last Authorization Observed |
| netpub.media | 14 | 67 | 67 | 2024-04-09 | 2025-01-14 |
| adsparc.com | 4 | 39 | 4 | 2022-03-13 | 2025-01-14 |
| digitalgreen.es | 3 | 34 | 3 | 2022-07-04 | 2025-01-14 |
| luponmedia.com | 45 | 32 | 44 | 2023-06-30 | 2025-01-14 |
| aralego.com | 29 | 29 | 30 | 2021-10-24 | 2025-01-14 |
| pixfuture.com | 44 | 29 | 30 | 2021-01-11 | 2025-01-14 |
| ucfunnel.com | 29 | 29 | 29 | 2024-05-08 | 2025-01-14 |
| adiiix.com | 27 | 27 | 27 | 2024-05-24 | 2025-01-14 |
| themoneytizer.com | 7 | 27 | 13 | 2022-09-24 | 2025-01-14 |
| purpleads.io | 4 | 22 | 22 | 2022-04-27 | 2025-01-14 |
Of those ad systems listed above, the following also appear listed as managers in Nakamas Web SL ads.txt files: themoneytizer.com, luponmedia.com, and netpub.media
This tab can also be useful in identifying historical sellers of this inventory, of which there are too many to specifically name & discuss in this post. We’ll be citing examples not featured in this top 10 subset of the table throughout the post.
One other ad system which currently authorizes several Nakamas domains by name, and which has an entire section of the ads.txt file devoted to them as identified by the comments (example below) is Bidgear.

As I mentioned in the previous section, there’s an easy way to use this sellers.json data to stay current on active laundering fronts (at least for now). Netpub.media seller “43dd158278e416e96d7e1e8efe878f1b” lists every laundering front by name the moment they are active. You can see this by filtering to that ID in the “Adsystems Authorizing By Name – Historic” tab, and comparing the first seen date to a similar web report for recent data, as I have done below:

As we can plainly see, the first day this domain is authorized in Netpubs sellers.json file is the first day traffic goes above 0… all the way to over 100k visits.
Direct Ads.txt Entries Which Can Be Matched to Sellers.json
We have identified ~5,500 unique ads.txt entries that the publisher denotes to be directly controlled accounts, and which can be matched to a corresponding sellers.json file using very relaxed matching criteria; regardless of agreement between declared seller / account types, we’re just looking for ads.txt ad system & publisher account ID to be matchable to a seller ID in the corresponding ad system’s sellers.json file. You’ll find the full results of that matching exercise in the “Verifiable Direct Ads Txt Rows” tab of the companion research sheet. This is a relatively weak signal of association @ business level, but can be helpful in confirming the relevance of associations we see from other datasets.
First thing we did to this data was truncate it such that content domains mentioned in matching sellers.json entries would be flattened & grouped under the label “some_content_domain.” This is necessary to reduce repetition in the dataset; we have relevant content domains available in the “Adsystems Authorizing By Name – Historic” tab we mention in the section above. The purpose of this dataset is to find possible first nodes in the supply chain. On its own, this dataset is not strong enough to be considered evidence of which paths are active, but we’ll reference this later to confirm signals we get from header bidding wrappers & other adtech network requests.
Useful On-page Signals:
Our crawlers are always listening to network requests as we visit sites, and periodically polling prebid wrappers for diagnostic signals that can be useful in our quality investigations. In this section, we’ll provide interesting signals from those datasets which get us closer to identifying Nakamas Web’s monetization partners over time. We’ll be most focusing on the recent trends in monetization, as this post could go on forever, and we want to make sure the most pressing info is presented without testing your attention span too much. If you have concerns you may be a damaged party, feel free to reach out, and we’ll help you parse the companion data to find relevance to your org if it exists.
Header Bidding Wrappers Detected and their Associated Ad Tech Vendors
Many ad managers & monetization partners provide their member publishers with the technology needed to get selling ASAP, including header bidding wrappers. These wrappers can tell us important information about the vendors who it relates to, and which accounts they use to sell inventory:
- The default prebid implementation uses the “pbjs” namespace, but sometimes wrappers use a unique namespace that denotes a particular vendor’s technology. This can be determined through forensic code analysis, and (rarely) these namespaces are described in documentation from the associated vendor.
- For example: adtelligent notes you should see “vmpbjs” object exist in the chrome console if their header bidding scripts are integrated correctly.
- Header bidding wrappers are often configured to include a certain supplyChain node with each request, and this can be extracted using the right commands. By matching the info contained in this sChain node to the relevant sellers.json file we are able to learn which organization is facilitating the sale of inventory.
We have compiled a table of all the wrapper / sChain configurations we saw on Nakamas Web Laundering fronts, and made it available in the “HB Wrapper Info” tab of the companion data sheet. One thing to note about this data: it’s become clear from our manual review of these properties that they are quite antagonistic to observers, and the prebid event log from some of these wrappers is aggressively scrubbed during visits. As a result, we may not have specific info on which bidders were actively participating in each auction, but it does not affect our ability to measure when these wrappers are in use, or which bidder modules could be used.
That said, these are the wrappers that gave us some additional information (either by name, or by sChain), and were measured to be live in the past 30 days:

Confirming what we saw in the ads.txt / sellers.json signals, Netpub appears across dozens of these sites, and their wrappers have been observed since early 2024. Unfortunately, these are some of the very antagonistic wrappers we mentioned, and we didn’t get an associated supply chain object. That being said, it’s not entirely a secret who Netpub’s key partners are, their corporate website makes it clear that they provide publishers access to premium demand via Criteo, Outbrain, and AdX.

Furthermore, just scanning sellers.json files we can see 14 ad systems that list Netpub as a partner with “publisher” or “both” types (meaning they could logically appear as the direct node in a supply chain), and 9 others that consider Netpub a valid intermediary.
Besides Netpub tech, we also saw wrappers from PurpleAds and BidGear, further confirming what we suspected from initial analysis of ads.txt and sellers.json information.
Additionally confirming what our eyeballs can tells us from visiting these sites (exemplified in the video and in my earlier screenshot from a laundering page), Infolinks is part of the Nakamas Web supply chain, and our historical data points to this being the case since early 2024. Going back to the “Verifiable Direct Ads Txt Rows” tab in the companion data sheet, we can see that this ads.txt entry starting appearing in Nakamas Web laundering domains on January 16th 2024, and we first saw it confirmed in Infolinks’ sellers.json file the following day, but with an extremely suspicious entity name / domain: ADS Technology.
Infolinks 3412924: ADS Technology

Infolinks declares that this direct account ID is controlled by by ADS Technology, an IT firm which provides no specific services in this industry. What’s more, we searched our database of network requests and found that Infolinks requests associated with PID 3412924 ONLY appear on Nakamas Web SL laundering fronts. Furthermore, there is no other ad system on earth listing a seller with that domain, so who the heck are they?
This suggests one of the following cases:
- Nakamas Web SL lied about who they were when they applied for an Infolinks seller account, and nobody at Infolinks verified beneficial ownership information.
- Nakama Web SL actually has taken control of that domain, and used that access to create a believable reach-out to Infolinks.
- Someone at Infolinks knowingly fabricated fake seller information for the Nakamas Web’ sellers profile’s account in order to avoid blocking / scrutiny.
Maybe it’s none of the above, but it’s definite that someone’s hiding something here, and I very much doubt it has anything to do with actual employees of ADS Technology. As an additional check, we made sure this wasn’t a new domain that was setup to create the illusion this company actually exists; the Wayback Machine shows this domain has existed & looked much like this for many years.
Parsing Bid Requests for Publisher ID
One way we attempted to diagnose the “who” of it all was to extract pub IDs from SSP tags, and what we found largely confirmed what we saw in the previous described reports. While we don’t suggest the ordering / volumes here are any real indication of the sellers’ bidstream SOV, or that bids were submitted in response to these requests, seeing a certain seller appear across many laundering domains does help establish confidence they announced this inventory for sale across a certain time period. You’ll find this information & more in the “Extracted PubIDs” tab of the companion data sheet.

We can see a Vidoomy pbjs wrapper appears associated with a couple domains in the “HB Wrapper Info,” but they are mentioned in many more communications outside of a header bidding context until late 2024.
For the most part, the entities named here appear in the “Authorizing by Name” tabs, and this report really just gives us an alternative perspective on their popularity. For example, checking back into the “Adsystems Authorizing By Name – Historic,” we can see that there are 14 entries in Vidoomy’s sellers.json file that specifically name a Nakamas Web Laundering domain:

Signals from Partners / 3rd Party Analysts (UPDATED: 2024-02-05):
We don’t require logs from our partners, but we’ll be updating this report in the next week with data our partners & readers authorize us to share in the interest of industry collaboration. From our preliminary review, it seems we’re on the right track using the sources we’ve disclosed in the companion data sheet, though each entity’s share of YOUR bid stream may vary.
UPDATE:
Thanks to our generous readers, we were furnished with supply chain data from two major DSPs. Data from one DSP (“DSP A”) allows us to identify the entities who most often made this inventory available for sale going back to 2021; data from the other (“DSP B”) describes the period immediately following the publishing of our research, and it was fascinating to see how the seller makeup shifted dramatically after our posting.
Since the time we posted, 8 new Nakamas Web SL sites were set live, and each one was authorized by Netpub the same day, just like we describe in the section devoted to sellers.json analysis.
Sellers are described in terms of the domain presented when matching a pubID to its relevant sellers.json file. Their respective yearly SOV will fall into 1 of 4 buckets:
- Sellers with 50%+ yearly avails SOV
- Sellers with 25%+ yearly avails SOV
- Sellers with 10%+ yearly avails SOV
- Sellers with 1%+ yearly avails SOV
Historical Data from “DSP A”
Data from this contributor allows us to identify the top sellers (split by direct, and reseller) of Nakama Web SL inventory for each year since 2021.
Here is the breakdown of top direct sellers for each year below:

In our first party data, we could most confidently speak to recent monetization practices, and DSP A’s report on direct sellers largely echoes what we saw as well: Netpub and Bidgear are most often bringing this inventory to market.
It is interesting to see just how much the primary sellers have shifted over time; to me, this suggests that there’s a smaller and smaller pool of managers / sales houses willing to represent this inventory. As we can see, a dozen different sellers have brought this inventory to market over the years in volumes exceeding 10%+ of the yearly SOV in any given year. Any one sellers doesn’t seem to stick around very long, making it a problem that’s not entirely solved by blocking any 1 seller. You should block sellers, AND domains in this case.
Here is the breakdown of top resellers for each year below:

As we noted earlier in this article, Infolinks’ presence in the monetization stack was hard to miss, and they certainly represented a large share of the reseller inventory in 2024. However, that was not always the case; just like the direct chart, we can see that the reseller makeup has changed much over time. If I had to guess, it’s driven by different connections to resellers each direct monetization partner brought to the table at the time.
UPDATE (2025-02-11):
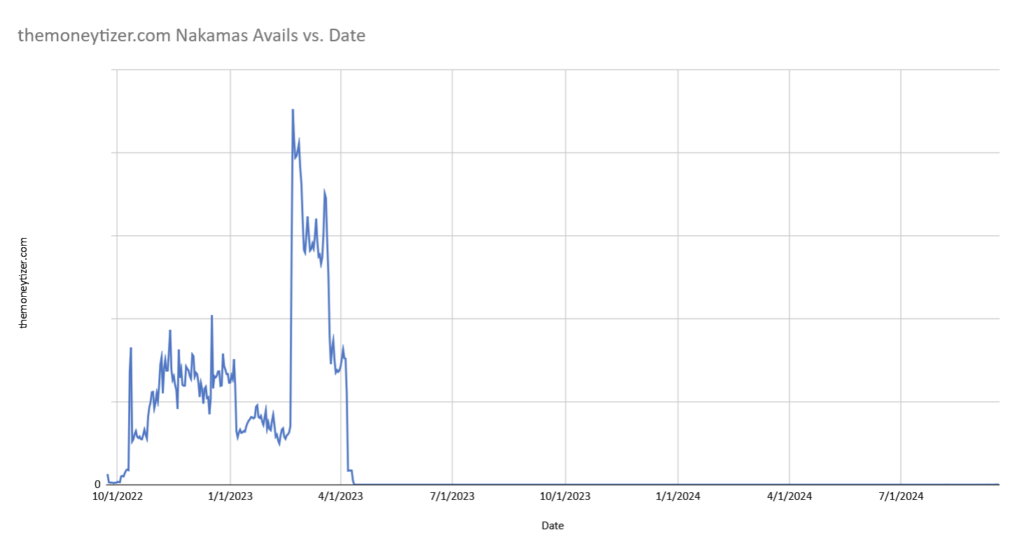
In the summary data from “DSP A” we identified that the seller domain “themoneytizer[.]com” (the ad system domain of “The Moneytizer”) was associated with a relatively small share of Nakamas Web SL announcements in 2022 & 2023.
In April 2023 we began working with The Moneytizer, and we helped them to successfully identify the Nakamas Web SL network sites. They immediately & effectively cut off monetization on these sites, and this screenshot related to TMZ in “DSP A” serves as confirmation of this timeline:
Recent Data from “DSP B”
“DSP B” sent full supply chains for opportunities they’ve been presented since our research dropped. It was pulled with a 7 day look-back window from January 28th 2025; this makes it almost entirely distinct from what “DSP A” sent us, and you should not expect trends to line up between the two.
Just like for “DSP A,” I broke out the reporting by direct vs reseller supply chain nodes.
Here is the breakdown of top direct sellers for the 7 days following our research-drop below:

It is not entirely surprising to see Bidgear and Netpub as the most prominent direct nodes, though I’m not sure what to make of seller “pgammedia.com” being the 2nd most prominent direct seller of this laundered inventory, and via Freewheel no less.
Furthermore, it’s interesting to see dailymotion / nsightvideo appear in this dataset as direct sellers, when they appeared as low-rate resellers in data from “DSP A.”
There is an immediate action item here for any SSP / AdSystem which authorizes accounts for suspicious managers / sales houses we’ve identified in this research: do yourself a favor, and review those partnerships. This stuff is only able to be resold because bad actors are able to announce this inventory using your pipes, and you connect to other premium exchanges, thus exacerbating the problem.
Moving along now to the of top resellers for the 7 days following our research-drop below:
When constructing this breakdown, we found it useful to contextualize each node in terms of who sold them the impressions (the preceding node in the supply chain). As such, we have constructed something of a new way of describing a sChain node, call it sChain node+ if you will. Grouping by that, we found something interesting: certain sChain node+ patterns only appear as middlemen, and certain sChain node+ patterns only appeared as the final node(s).This could be due to traffic shaping by sellers w/ respect to this particular DSP, or something else entirely.
Here we can see the middlemen:

So we already know from the research as a whole, and from the above direct data, that Netpub is a prominent manager of this inventory. It seems they most often turned around and made that inventory available to other resellers via adagio pipes.
There is an interesting sChain participant that we didn’t really identify in our independent research: xapads. They appear to be originating a fair bit of this inventory via amazon APS, and then it’s being resold via Smaato pipes.
And here we can see the final sellers:

There were more unique terminal nodes than direct nodes, as we could reasonably expect. The most common path used to bring this shady Netpub inventory to “DSP B” went through Criteo / themediagrid.com; this makes sense given that Netpub considers them a key partner, and touts that partnership on their corporate home page.
To me, this is one of the most important images in the whole article: it shows exactly how this inventory filters from dishonest direct sellers to premium exchanges. For example: in rows 2 & 4 we can see that Magnite pipes are used by R2B2 & Seedtag to resell crappy Bidgear inventory in relatively high amounts. The inventory would never meet Magnite’s own guidelines for direct partnership, but it doesn’t matter when the resellers Magnite authorizes have much lower standards.
Again, it is good to see that the Infolinks paths are only a tiny share of the volume now. It’s clear from seller.json analysis that Infolinks has de-authorized the offending accounts, and so they should no longer be able to access premium demand that way.
Conclusion
Despite identifying a single beneficial owner across all the laundering fronts & pirate content directories, the massive number of individual sellers & resellers makes it extremely hard to hold Nakamas Web SL accountable for the invalid inventory they’ve been peddling for years.
We have, to our best ability, presented indicators of which organizations facilitate the sale of this ill-gotten inventory, and we hope it helps the affected members of the supply chain to hold them accountable. Almost every SSP / Exchange is affected to some degree, even if they don’t have a pub-direct connection to Nakamas Web, because the managers / sales houses representing the inventory have such a huge footprint.
Some of these sellers are repeat offenders; I remember working with Jounce in 2023 to identify the sellers putting the most pirate inventory into the bidstream, and some of those same sellers appear in this report today. To quote that AdExchanger piece which covered that research:
“Jounce highlighted 17 piracy domains in a recent report, which found that 11 sellers regularly monetized these domains, including BidGear, PubFuture, PapayAds, Atlas Media, AdMaven, PurpleAds, Upzyde, VidCrunch, Ad+, FatChilli and Z1 Media.“
https://www.adexchanger.com/ad-exchange-news/how-can-advertisers-stop-funding-piracy-block-sellers-not-domains/
Chris Kane, the CEO and founder of Jounce, with whom we worked to produce the above-cited research, had this much to say after reviewing our new research:
“There is a years-long history, documented by DeepSee, that certain sellers are in the business of monetizing copyright-infringing content. Any SSP that partners with these sellers is at best lacking proper governance and at worst willfully facilitating piracy.“
The clearest way to prevent the next version of this scheme is to be aware of managers & other inventory-aggregators with poor standards out of these exchanges. That much is already possible today. For example, it takes just a moment for us to produce this list of manager domains listed on >=15 root domains, and which we have >=10% of those domains flagged as piracy:

These are manager domains we extracted from ads.txt files. The ones tagged in yellow operate header bidding wrappers we’ve identified in use on these Nakamas Web laundering pages, or explicitly authorize such a domain by name.
Are you a reseller looking to clean up the partners you source from? Happy to help.
Supplemental Data
Here you will find the worksheet wherein I’ve compiled the evidence used in the video & in this post. Everything is made available “as is” with no guarantee that any report is representative of the exposure relative to your organization, or the industry at large. I hope it helps you track down any exposure you may have, and helps in untangling this messy scheme.